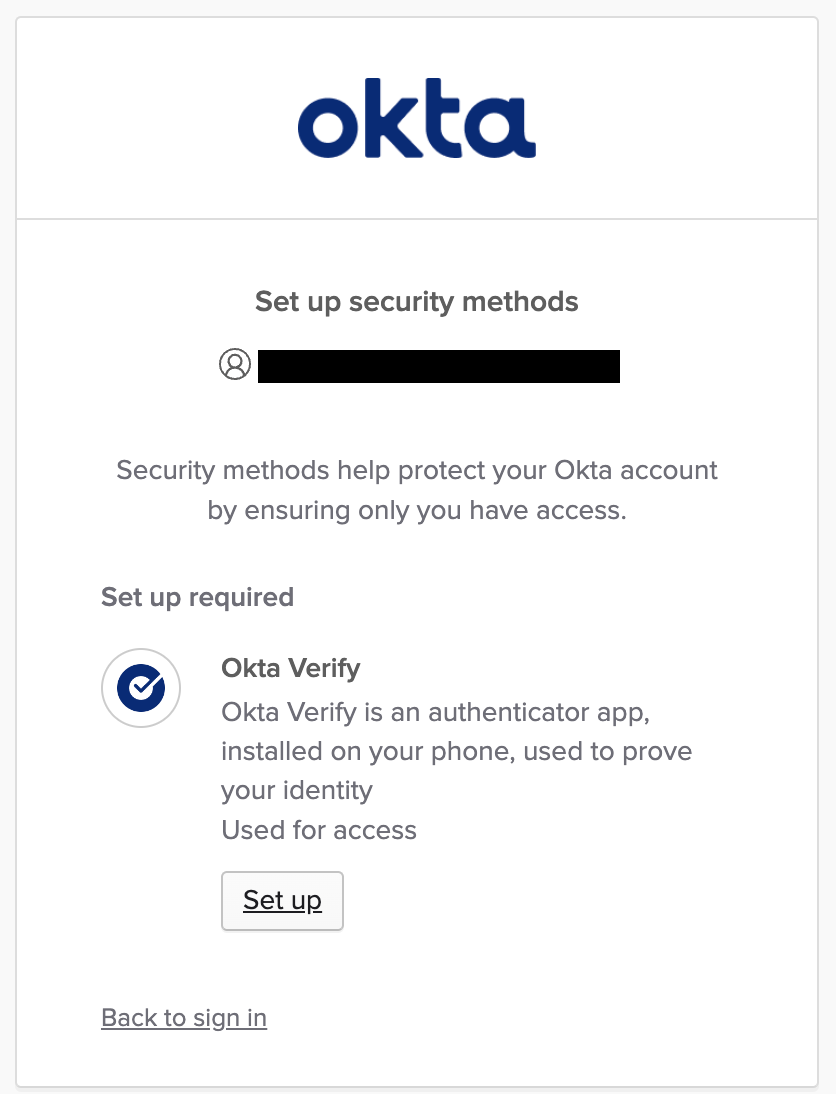
Enable MFA in Okta
In this use case, you will enable MFA with Okta Verify for every login to Okta and therefore to AWS IAM Identity Center.
Why introduce MFA?
Identity is the new perimeter and organizations introduce MFA to better protect access to applications and services.
Why Okta?
Just having a MFA solution is not enough, Organizations must be able to integrate it in a secure way for all applications. Okta provides over 7500 SSO Integrations for Cloud and On-Premise Applications. Okta protects all those applications with MFA and if you don’t find them on the Okta Integration Network (OIN) , Okta supports open standards and other integration methods.
Introduction a second factor adds friction to the end-user experience. With Okta’s adaptive Multi-Factor Authentication , Organizations define based on risk and context the right balance of security and user experience.

Okta provides a wide variety of vendor neutral factors . Here are a few:
- Okta Verify: Smartphone App for Android and iOS that supports user-friendly Push Notifications and OTP
- U2F, FIDO2 & WebAuth: e.g. biometric authentication with Apple TouchID, Windows Hello and YubiKey
- Google Authentication
- Magic Link and OTP via Email
- OTP via SMS
- Integration of existing hardware tokens, legacy MFA solutions and OATH-OTP
- Passwordless authentication, Certificates and more
Configuration Steps: Add Okta Verify Authenticator
-
Open the Okta Admin Console, go to Security -> Authenticator and click on Add Authenticator.

-
Click Add of Okta Verify. Okta supports even more Authenticators than the ones shown here, but they are not available as part of the free trial. If you have a MacBook with TouchID, WindowsHello or a FIDO-compatible key like a YubiKey, you can also enable FIDO2 (WebAuthn).

-
Select in the configuration dialog of Okta Verify
- Push notification (Android and iOS only): This will allow using a push notification next to an OTP with the Okta Verify App on iOS and Android.
- Okta FastPass (All platforms): This will allow passwordless login with the free Okta Verify App available on Mac, Windows, iOS and Android.
- Show the “Sign in with OktaFastpass” button: This will allow passwordless login with Okta Verify without entering a username or password.

- Who and when the MFA enrollment is allowed can be configured in the tab Factor Enrollment. A default configuration is provided and fine for the workshop.
Configuration Steps: AWS IAM Identity Center Sign-On Policy
The next step is to enforce MFA for the AWS IAM Identity Center Application.
-
Go to Applications -> Applications and select the AWS IAM Identity Center Application
-
Switch to the tab Sign On, scroll down and click on View policy details.

-
A Default Policy was automatically assigned to the AWS IAM Identity Center Application. This policy is shared across multiple applications. For simplicity, we will enforce MFA for all Applications, but you can also create a dedicated Policy just for AWS IAM Identity Center.
-
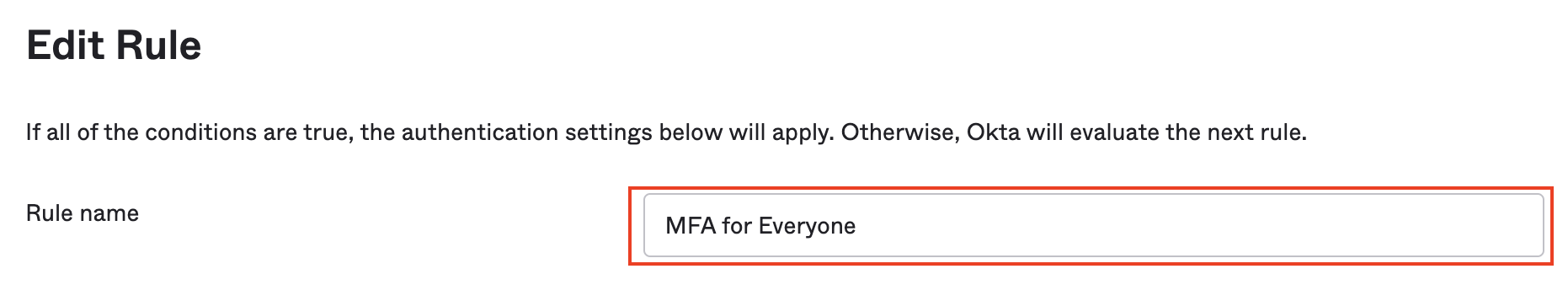
Click on Add rule.

-
Enter the Rule name MFA for Everyone.
-
Select Possession factor. Okta will automatically show all the authenticators that are enabled in your Okta tenant that have the factor type possession.

-
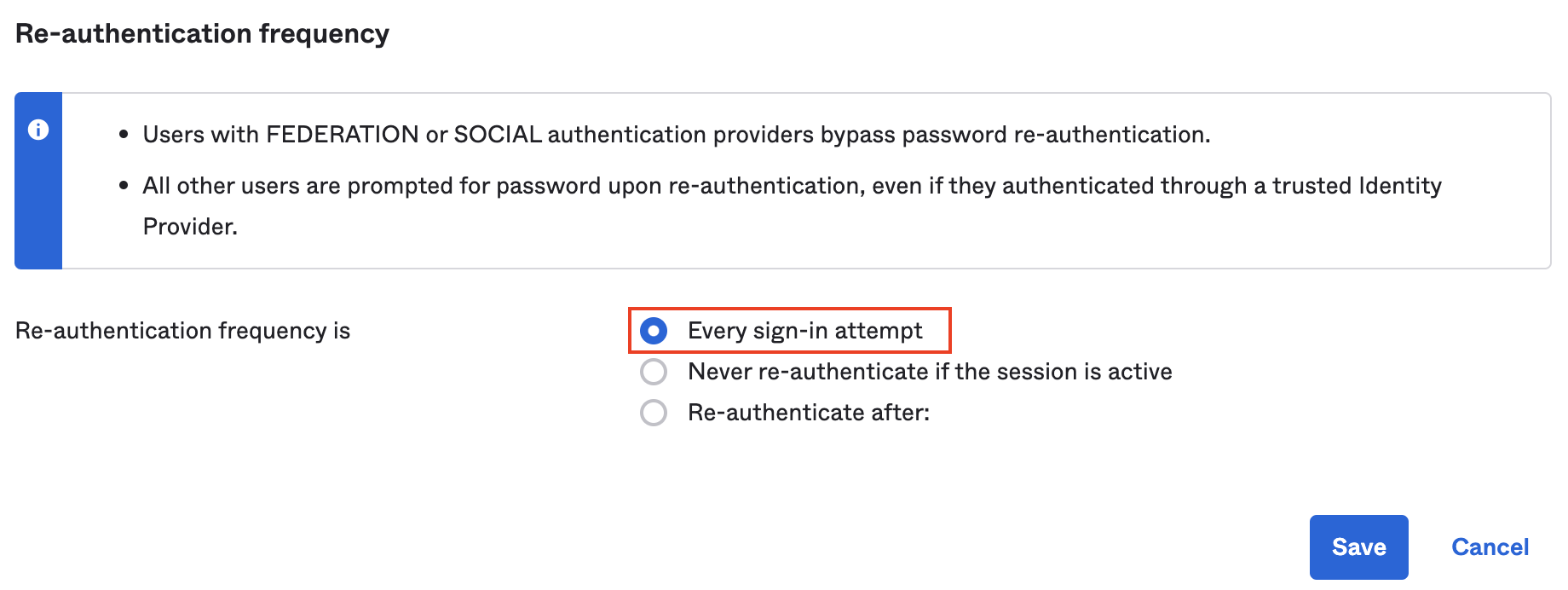
To enforce MFA on every login, select Every sign-in attempt and click on Save.
-
That’s it. Okta will prompt you on the next login to enroll your MFA (Okta Verify) and on the following logins, you must use it.
Test
-
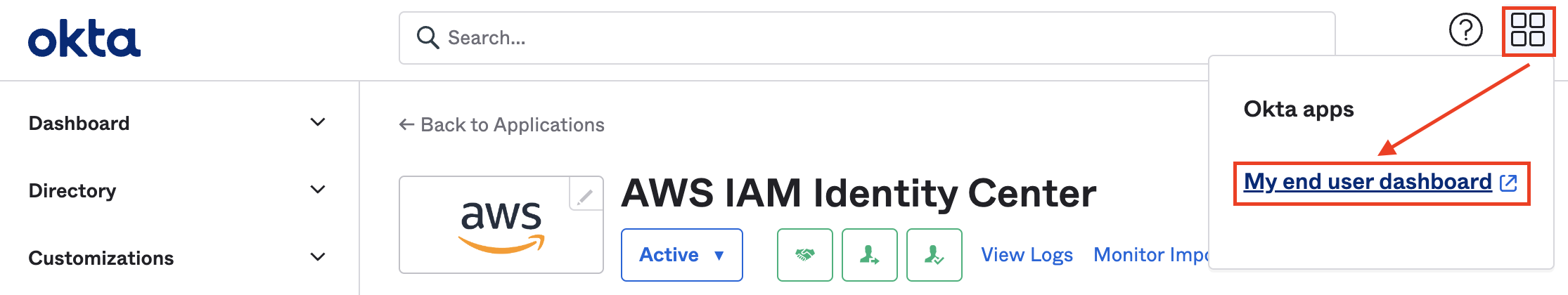
Go to the End User Dashboard.
-
Click on the AWS IAM Identity Center Application.
-
The first time you sign in, you will be prompted to enroll in your MFA (Okta Verify).